API security is critical to protect sensitive data, maintain the integrity of services, and prevent unauthorized access. It's a fundamental aspect of modern software development, especially as organizations increasingly rely on APIs to connect and share data between systems and applications.
Here are some tips to help you secure your APIs effectively:
1. Authentication and Authorization:
Authentication
Implement strong authentication mechanisms to verify the identity of clients accessing your API. Use methods like API keys, OAuth, JWT (JSON Web Tokens), or client certificates.
Authorization:
Control what actions each user or client can perform within your API. Enforce fine-grained access control to limit unauthorized access to resources.
- Tip: Implement strong authentication and authorization mechanisms to control access to your API.
- Example: Use JSON Web Tokens (JWT) for authentication. Libraries like
jsonwebtokenhelp create and verify JWTs in Node.js.
const jwt = require('jsonwebtoken');
// Create a JWT
const token = jwt.sign({ user: 'john.doe' }, 'secretKey', { expiresIn: '1h' });
// Verify a JWT
const decoded = jwt.verify(token, 'secretKey');
2. Use HTTPS:
Always use HTTPS to encrypt data in transit. This prevents eavesdropping and man-in-the-middle attacks, ensuring data confidentiality and integrity.
- Tip: Use HTTPS to encrypt data in transit to ensure data confidentiality.
- Example: When making API requests in the browser, use the
fetchAPI over HTTPS.
fetch('https://api.example.com/data')
.then(response => response.json())
.then(data => console.log(data))
.catch(error => console.error(error));
3. Input Validation:
Sanitize and validate all input from clients to prevent common vulnerabilities like SQL injection and cross-site scripting (XSS).
Tip: Sanitize and validate input data to prevent security vulnerabilities like XSS and SQL injection.
Example: Use a library like validator to validate and sanitize input data in a Node.js application.
const validator = require('validator');
if (validator.isEmail(req.body.email)) {
// Valid email address
}
4. Rate Limiting:
Implement rate limiting to prevent abuse of your API. Limit the number of requests a client can make within a specified time frame to protect against DoS attacks.
- Tip: Implement rate limiting to prevent abuse of your API.
- Example: Use a library like
express-rate-limitto set rate limits for API endpoints in an Express.js application.
const rateLimit = require('express-rate-limit');
const limiter = rateLimit({
windowMs: 15 * 60 * 1000, // 15 minutes
max: 100, // limit each IP to 100 requests per window
});
app.use('/api/', limiter);
5. Data Encryption:
- Encrypt sensitive data at rest using strong encryption algorithms. Protect API keys and other credentials stored on your servers. Encrypting data in JavaScript can be achieved using various encryption libraries and algorithms.
- Below is an example of how to encrypt and decrypt data using the CryptoJS library in a Node.js environment.
- CryptoJS provides various encryption algorithms such as AES, DES, and more.
First, make sure to install the crypto-js package:
npm install crypto-js
Now, you can create a JavaScript script to encrypt and decrypt data:
const CryptoJS = require('crypto-js');
// Replace these with your own keys
const secretKey = 'your-secret-key';
const dataToEncrypt = 'Sensitive data to be encrypted';
// Encryption
const ciphertext = CryptoJS.AES.encrypt(dataToEncrypt, secretKey).toString();
console.log('Encrypted:', ciphertext);
// Decryption
const bytes = CryptoJS.AES.decrypt(ciphertext, secretKey);
const decryptedData = bytes.toString(CryptoJS.enc.Utf8);
console.log('Decrypted:', decryptedData);
6. Error Handling:
Avoid exposing detailed error messages that can be exploited by attackers. Provide informative but generic error messages to clients.
- Tip: Handle errors securely without revealing sensitive information.
- Example: Use a custom error handler in Node.js to log errors while providing a generic response to clients.
app.use((err, req, res, next) => {
console.error(err);
res.status(500).json({ error: 'Internal Server Error' });
});
7. API Versioning:
API versioning is a common practice to manage changes in your API while maintaining backward compatibility. One way to achieve API versioning in JavaScript-based APIs is by including the version in the URL or headers. Here's an example using Express.js, a popular Node.js web application framework:
First, make sure you have Express.js installed:
npm install express
Now, create an example of API versioning in Express.js:
const express = require('express');
const app = express();
const port = 3000;
// Define two versions of your API
const apiV1 = express.Router();
const apiV2 = express.Router();
apiV1.get('/greet', (req, res) => {
res.json({ message: 'Hello from API v1!' });
});
apiV2.get('/greet', (req, res) => {
res.json({ message: 'Hello from API v2!' });
});
// Define routes with version prefixes
app.use('/v1', apiV1);
app.use('/v2', apiV2);
app.listen(port, () => {
console.log(`Server is listening at http://localhost:${port}`);
});
In this example, we've created two versions of an API, v1 and v2, and defined a /greet endpoint in each version. Clients can access the desired version by including the version in the URL.
For example:
- API v1:
http://localhost:3000/v1/greet - API v2:
http://localhost:3000/v2/greet
This allows you to introduce changes to your API while ensuring that existing clients using the previous version are not affected. Remember to update the routes and logic for each version as needed to accommodate changes or new features.
9. Security Headers:
Implement security headers, such as Content Security Policy (CSP) and Cross-Origin Resource Sharing (CORS), to control the behavior of your API in web browsers.
- Tip: Set appropriate security headers, such as Content Security Policy (CSP) and Cross-Origin Resource Sharing (CORS).
- Example: Configure CORS in your Express.js application to control which domains can access your API.
const cors = require('cors');
const corsOptions = {
origin: 'https://example.com',
};
app.use(cors(corsOptions));
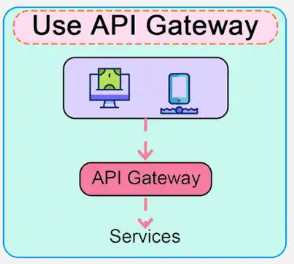
10. API Gateway:
Creating an API Gateway with JavaScript often involves using a web framework like Express.js in a Node.js environment.
Here's a basic example of how to create a simple API Gateway with Express.js:
First, make sure you have Express.js installed:
npm install express
Now, let's create an API Gateway with multiple routes:
const express = require('express');
const app = express();
const port = 3000;
// Define routes for different services
app.get('/service1', (req, res) => {
// Implement logic for Service 1
res.json({ message: 'Response from Service 1' });
});
app.get('/service2', (req, res) => {
// Implement logic for Service 2
res.json({ message: 'Response from Service 2' });
});
app.get('/service3', (req, res) => {
// Implement logic for Service 3
res.json({ message: 'Response from Service 3' });
});
app.listen(port, () => {
console.log(`API Gateway is listening at http://localhost:${port}`);
});
In this example, we've created an API Gateway with three different routes, each simulating a separate service. When clients make requests to /service1, /service2, or /service3, the API Gateway handles the requests and provides responses. This is a simplified illustration, and in a real-world scenario, you would route requests to separate microservices or backend services.
To create a more sophisticated API Gateway with features like request transformation, load balancing, and caching, you would typically use a dedicated API Gateway service or a more robust framework like AWS API Gateway or Apigee. These services provide more advanced features for managing and securing APIs in a production environment.
11. Access Controls:
Access control is essential for securing your JavaScript-based applications. You can implement access controls using JavaScript to restrict unauthorized access to certain parts of your application. Here's an example of how to implement access controls in a Node.js application using Express.js:
First, make sure you have Express.js installed:
npm install express
Now, let's create a simple example of access control:
const express = require('express');
const app = express();
const port = 3000;
// Simulate user roles (you would typically retrieve this from your database)
const userRoles = {
admin: 'admin',
user: 'user',
};
// Middleware function to check user roles
function checkUserRole(role) {
return (req, res, next) => {
if (req.userRole === role) {
next(); // Allow access
} else {
res.status(403).json({ error: 'Access denied' });
}
};
}
// Simulated user with a role
const user = {
name: 'John Doe',
role: userRoles.admin,
};
// Endpoint with access control
app.get('/admin/resource', checkUserRole(userRoles.admin), (req, res) => {
res.json({ message: 'Admin resource accessed' });
});
app.get('/user/resource', checkUserRole(userRoles.user), (req, res) => {
res.json({ message: 'User resource accessed' });
});
app.listen(port, () => {
console.log(`Server is listening at http://localhost:${port}`);
});
In this example, we've defined two user roles, "admin" and "user." The checkUserRole middleware checks the user's role, and if it matches the required role, it allows access. You can attach this middleware to specific routes, as shown in the /admin/resource and /user/resource routes.
Remember to adapt this example to your application's needs and integrate it with user authentication and roles retrieved from your database or authentication service for real-world scenarios.
12. Throttling:
API security is crucial to prevent abuse and unauthorized access to your APIs. While throttling is important for managing API usage, it is typically implemented on the server side rather than in client-side JavaScript. You would typically use an API Gateway or server middleware to implement throttling.
However, if you want to show a basic example of how you can rate-limit API requests in JavaScript for demonstration purposes, you can use the following code:
const express = require('express'); const app = express(); const port = 3000; const MAX_REQUESTS = 5; // Maximum number of requests per minute const THROTTLE_INTERVAL = 60 * 1000; // 1 minute in milliseconds // Create a data structure to store request timestamps const requestTimestamps = new Map(); // Middleware to implement throttling function throttleMiddleware(req, res, next) { const clientIP = req.ip; if (!requestTimestamps.has(clientIP)) { // If the client is making the first request, initialize the timestamp requestTimestamps.set(clientIP, Date.now()); next(); } else { const lastTimestamp = requestTimestamps.get(clientIP); const currentTime = Date.now(); if (currentTime - lastTimestamp < THROTTLE_INTERVAL) { // If requests are coming too quickly, return a 429 Too Many Requests status res.status(429).json({ error: 'Too Many Requests' }); } else { // If enough time has passed, update the timestamp and allow the request requestTimestamps.set(clientIP, currentTime); next(); } } } app.use(throttleMiddleware); app.get('/api/resource', (req, res) => { res.json({ message: 'API resource accessed' }); }); app.listen(port, () => { console.log(`Server is listening at http://localhost:${port}`); });
In this example, we've implemented a basic rate-limiting middleware using Express.js. It allows a maximum of 5 requests per minute from a single client IP address. If a client exceeds this limit, they will receive a "Too Many Requests" response (HTTP status 429). This is a simplified demonstration, and in a production environment, you would likely use a more robust API Gateway or middleware for implementing throttling and other security features.
13. Data Privacy:
Comply with data privacy regulations, such as GDPR, HIPAA, or CCPA, by securing the personal data processed by your API.
14. Security Best Practices:
- Stay updated on security best practices and follow industry standards. Regularly review and improve your security measures as new threats emerge.
- Train your development and operations teams on API security best practices.
- Security is a shared responsibility across your organization.
- Keep your API and its dependencies up to date with the latest security patches and updates.
- Regularly perform security assessments and penetration testing on your API to identify and fix vulnerabilities. Use tools like OWASP ZAP and Nessus to conduct thorough security tests.
- Set up robust logging and monitoring to track suspicious activity and potential security breaches. Monitor access, errors, and unusual patterns.
By following these tips and regularly assessing and enhancing your API security, you can significantly reduce the risk of security breaches and protect your data and users effectively.